Make sure your devices are up-to-date!

Introduction
The most important and difficult task is to keep your devices up-to-date with software and Windows. It's going to be very difficult if you manage it all manually, but luckily for us, Intune has Windows Update rings.
If you haven't looked into Windows Update Rings in Intune yet, then stop what you are doing and configure it with me later on!
Update Orchestrator Service
When we are talking about Windows Update, there is one service that we have to keep in mind. The service I'm talking about is the "Update Orchestrator Service".
The Orchestrator service runs automatically and makes sure that updates are applied to the device. If this service doesn't run, the updates can't be downloaded.
I would recommend you take a look at the below learn page, where the flow of the update orchestrator service is described.

Configuration
Let's get to the configuration of our Windows Update rings. Ideally, we would create more than one update ring, so we would have at least a pilot ring and a production ring. We will only dive into the basics, so we will only create one this time.
Start by jumping into the Intune portal, and head into "Devices" and "Update rings for Windows 10 and later".
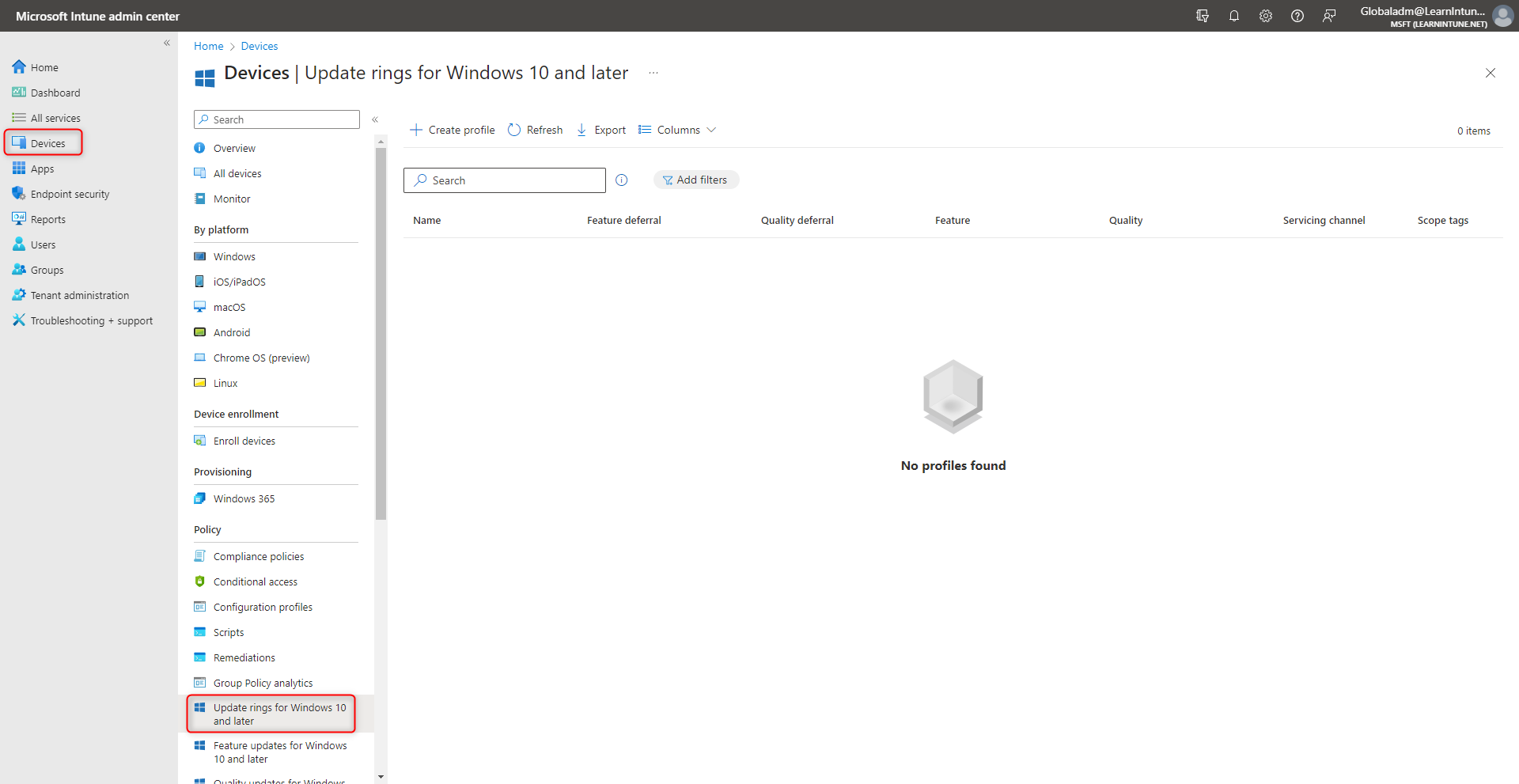
From here, we will create our profile. Click on "Create profile", name your profile as you like, and make sure to click next.
After you have clicked next, you can now see all the available update settings.
Update Settings
I will explain what the different settings do. It's important to note with update rings, that you can do it in many different ways. I will describe the settings, and let you configure it how you like it!
- Microsoft Product Updates
Microsoft product updates are updates to programs such as Microsoft Office or another Microsoft product.
- Windows Drivers
You have the option to allow or include driver updates in Windows updates. As Microsoft states, its non-Microsoft drivers 'relevant' to your device.
- Quality and feature update deferral period (days)
I have chosen to put the deferral period for both quality and feature updates in the same. These two settings define how many days you would like to wait before the quality and feature updates become available for end-users.
Feature updates: Feature updates are the updates, that will add the big changes on your devices.
When setting the deferral period, it's a good idea to take into account that feature update deferral periods should be longer than quality updates. This is because feature updates contain big updates that could potentially cause issues.
- Update Windows 10 devices to latest Windows 11 release
As the name states, it will update Windows 10 devices to the latest Windows 11 release. It's important to know that this will only impact devices eligible for Windows 11.
If your device doesn't fit the requirements for Windows 11, it won't try to update.
- Set feature update uninstall period
For this setting, you define the number of days that a device can uninstall feature updates. Let's say that we've configured this for 10 days. If you want to uninstall a feature update after 15 days, the device won't allow you to.
- Enable pre-release builds
If you want to allow your devices to get updates that aren't fully available yet, you can participate in the Windows Insider channels.
Be aware that this could cause some issues, and I won't recommend this for production.
User Experience Settings
- Automatic update behavior
There are six different behaviors that a device can have. I will explain 'Auto install and restart at maintenance time'.
With the auto-install and restart at maintenance time behavior, the updates will automatically download,checking outbut some updates won't install before the device has been rebooted. The active hours will define when a device can reboot.
If you are interested in checking out the other behaviors, I would recommend you take a look here:

- Active hours start / end
The active hours are the time when a device won't be able to reboot. The standard active hours are 8 AM to 5 PM, within that time the device can't reboot. However, if the user doesn't reboot within the deadline and grace period, this doesn't apply.
- Option to pause Windows updates
You can enable or disable it if the user should be able to pause Windows updates. I would recommend, that you disable this setting.
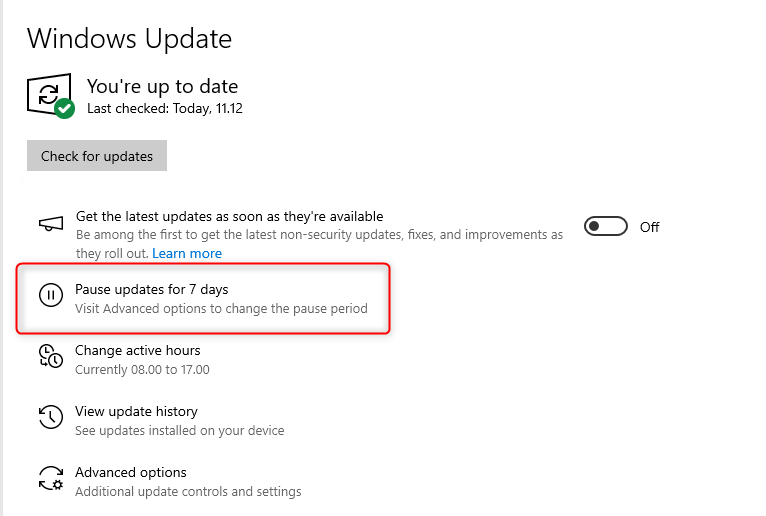
- Option to check for Windows updates
It would be lovely if a user voluntarily checked for updates now and then, but unfortunately, that isn't the case. I think it should be available for the user anyway! 😎
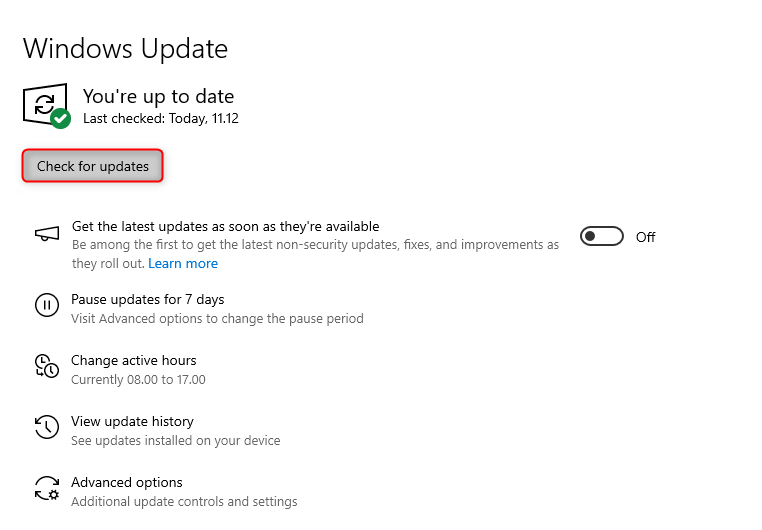
- Change notification update level
There are 4 different options within this setting:
- Use the default Windows Update notifications
- Turn off all notifications, excluding restart warnings
- Turn off all notifications, including restart warnings
I would keep the Windows Update notifications, so the user is aware of the device is updating and information about eventual reboot of the device.
It's also an option to keep the restart warnings only, but also remove all notifications.
- Deadline settings
- Feature updates/quality updates
The deadlines for feature and quality updates are in place, for the users that just won't update their device. If the deadline has passed, the device will force the updates to be installed.
- Grace period
A grace period is in place when the updates have been installed, and the device has a pending restart. It's however important to know, that it's taking the number of days from the deadline setting plus the grace period.
- Auto reboot before deadline
With this setting configured to yes, the device will reboot before the deadline has expired. If you have configured this to no, the device will wait to reboot after the deadline has expired.
Example of a Update Ring
As a example I have configured a update ring, that I wanted to share with you. You can see the settings of the update ring, in the below picture.
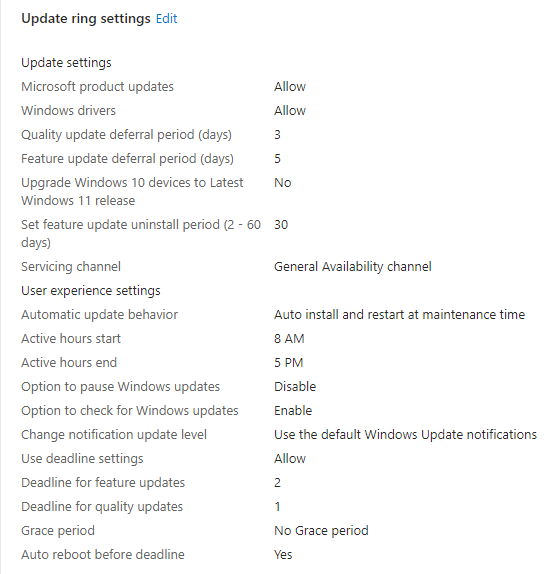
I would recommend to create at least a pilot and a production ring, if you aren't only creating a update ring for testing purposes.
Let's start the testing!
We will get started on the testing, and see how it looks when our update ring has been applied. I have spun up a VM with Windows 21H1, and the policies have been applied.
I tricked the VM a little and configured the date to one day ahead (deferral has been configured 1 day) and it gave me the below notification.
Which is the default Windows Update notification, that's great.
Once I saw the above notification, I headed into the Windows Update settings and saw that it started the download of all my missing updates.
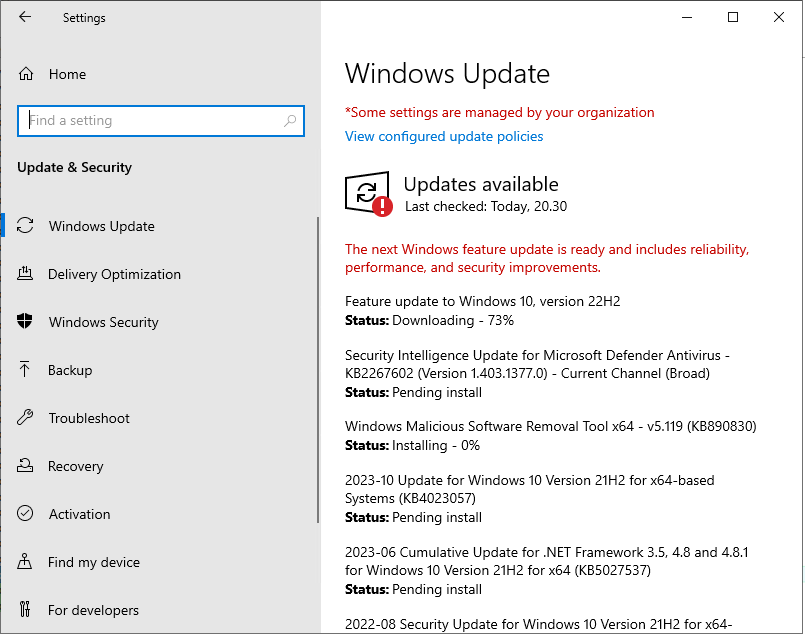
Wooow! I'm missing a lot of updates.....
After my internet connection had been good to me, and the updates had been installed, it gave me this notification.
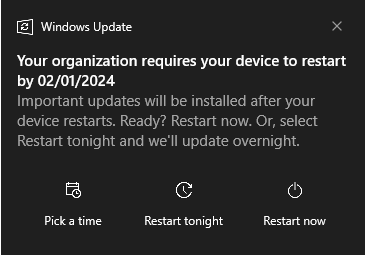
As the lousy employee I am 😎, I don't want to restart before 02/01/2024. So I tricked the date a little bit more, and I wanted to check what happened.
Some minutes before the device is forced to restart, it gives me the below reminder.
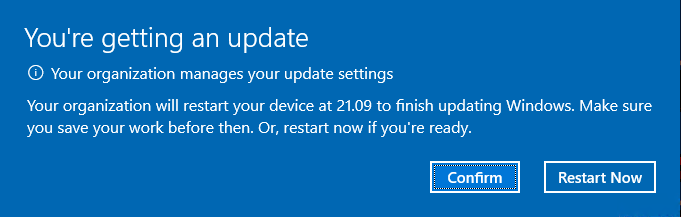
A few minutes later the clock changed to 21:09, and the device began the restart.

How can I see that my policies have been applied?
There are several ways to confirm, that your policies have been applied to a device. First of all, there is the traditional way of checking it through the Intune portal.
The next way, I want to show is under "Access work & school" on a device. If you click on "Info".
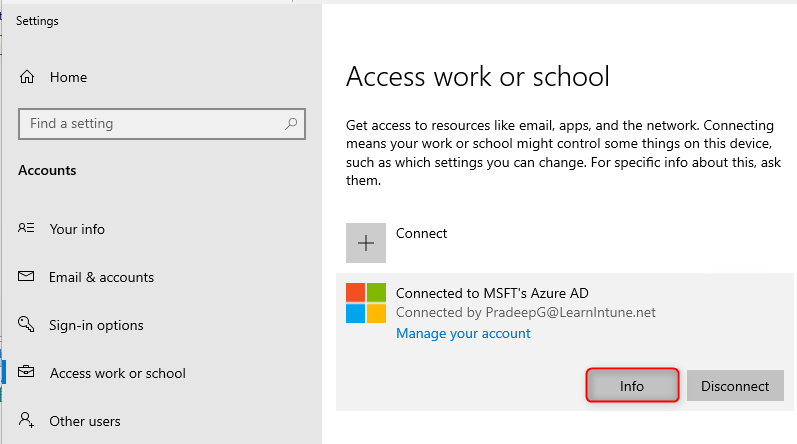
From the info page, can you see which policies have been applied to the device. As you can see below, the update policy has been applied.
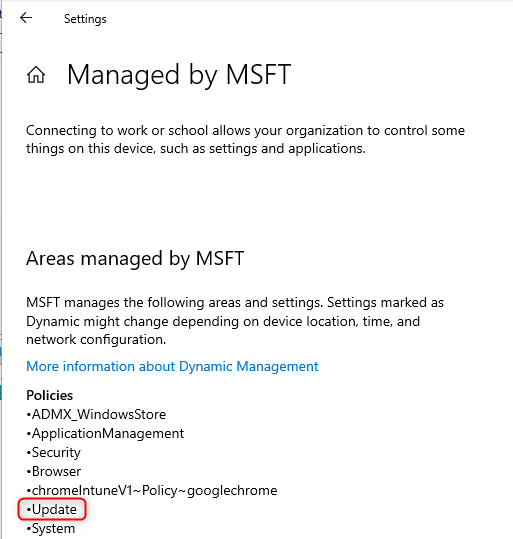
Another place you can see whether the update ring has been applied or not is within the registry editor.
Open the registry editor and paste this path.
'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\Update'
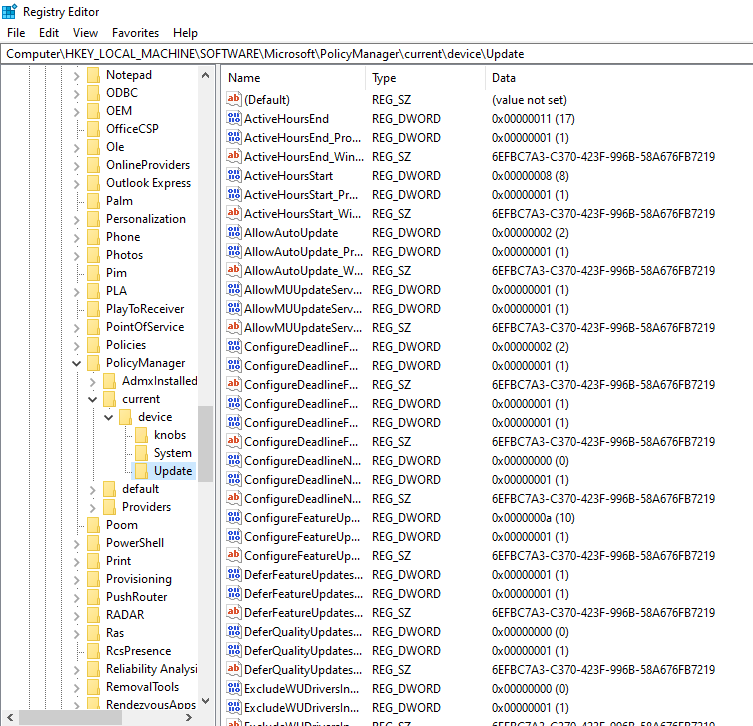
All the settings from your update ring are available within this path.
What about troubleshooting?
If you are experiencing issues with the administration of Windows updates, I would recommend you take a look at the log files. The log files are a .etl extension, which you can find at this location: "C:\Windows\Logs\WindowsUpdate".
If you wish to take a deeper look at the logs, you can collect all .etl files into a single .txt with a PowerShell command: "Get-WindowsUpdateLog".
Conclusion
Thank you for reading this blog. It's a blog post that has been made for beginners, who would like to set up their first update ring. I hope that my explanations made it easier, to set up your rings!
