BYOD: The next step with MAM

Introduction
In my other blog post, I wrote about the situation with BYOD and personally-owned devices and how it's possible to protect corporate data on these devices.
We took a closer look at the App Protection policies and how the experience was for the end-user. Now, we have control with Edge, but what about the Office desktop apps? Technically, the end-user can still access the Office desktop apps, there isn't anything preventing them from doing so.
Let's get at it while it's fresh in our memory!
Configuration
All the hard work has already been completed, and you now have a test device enrolled with MAM. The goal now is to prevent the end-user from using the Office desktop apps.
The first step is to head to Conditional Access policies and create a new policy. I have named my policy "BLOCK: Office Desktop Apps on BYOD Devices" and included my test user.
Once that's done, we will have to target Office 365 in our target resources.
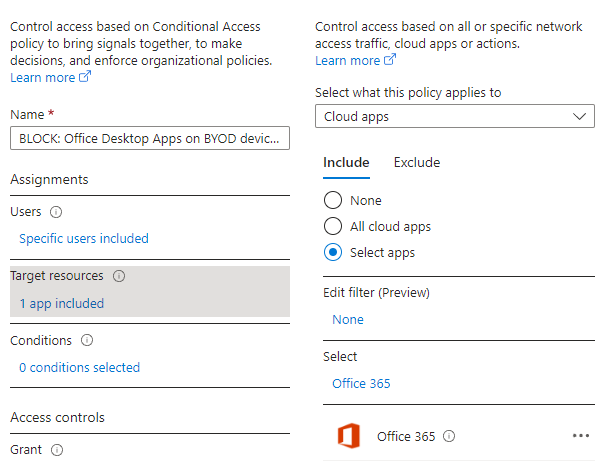
Next up are our conditions. Do you remember the conditions from the last blog? It's the same conditions but with a few modifications. First, start with device platforms and include Windows.
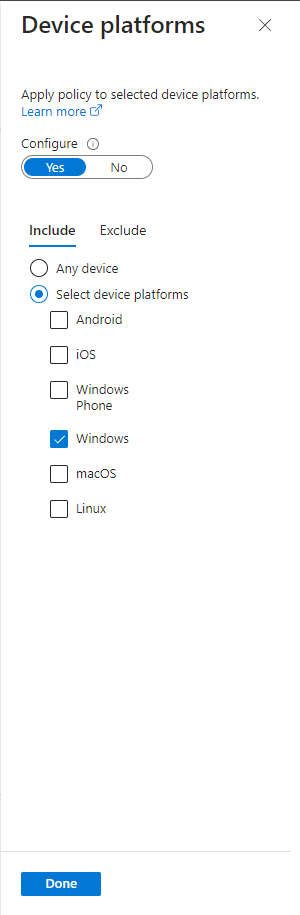
Device platforms are now configured, and the next is client apps. It's very important that we select all options UNLESS browser.
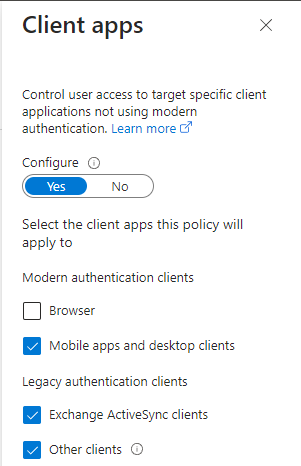
We want this policy to apply whenever a user uses other apps than the browser.
Client apps and device platforms are now configured, and if you remember correctly, we still need the filter for devices!
I would like all devices that aren't "Entra Hybrid joined" or "Entra joined" to be included in this policy. Did you remember from the last blog that devices that are MAM enrolled are "Entra registered"?
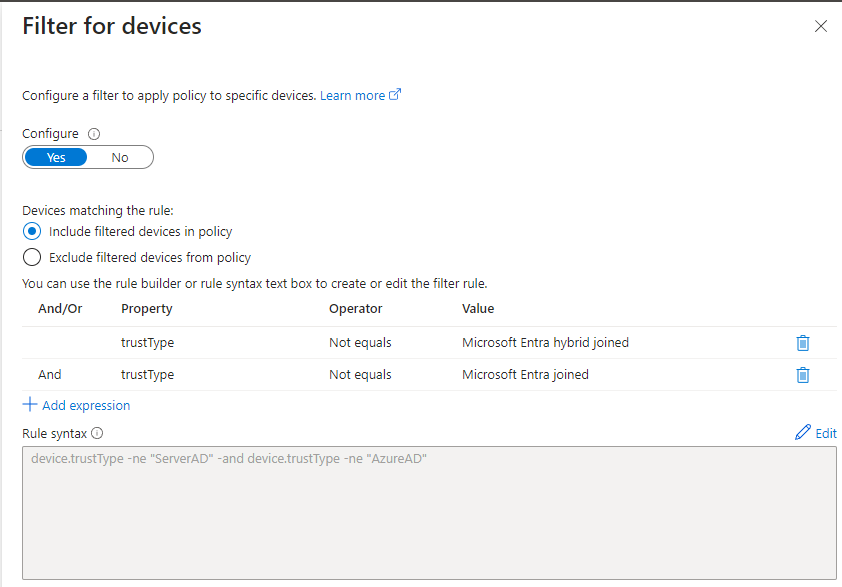
All our conditions are now configured, but before we can create this policy, we have to clarify our controls.
I would like to grant access and "Require device to be marked as compliant". As shown in the picture below.
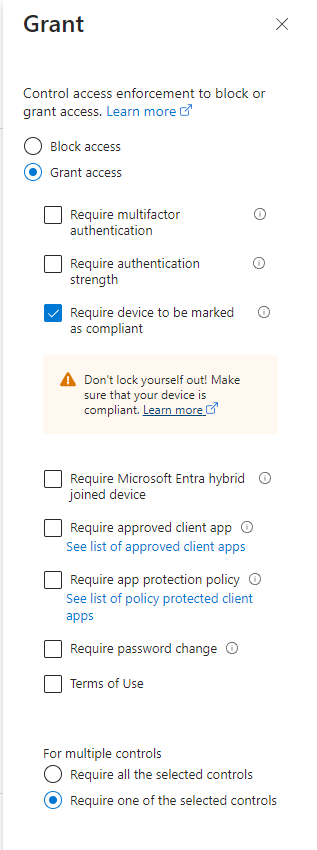
You might think, why do I decide to do that? I could choose to pick another, such as "Block access", it would give the same result.
An "Entra registered" device will never be compliant, so that's why I chose that. I could also block access because I have filtered out all "Entra joined" and "Entra Hybrid joined".
The policy is now finished, and you can click Create.
Let's get the test going!
I have the VM turned on and made sure it's MAM enrolled. I have downloaded Office, and I will now try to log in with my user.
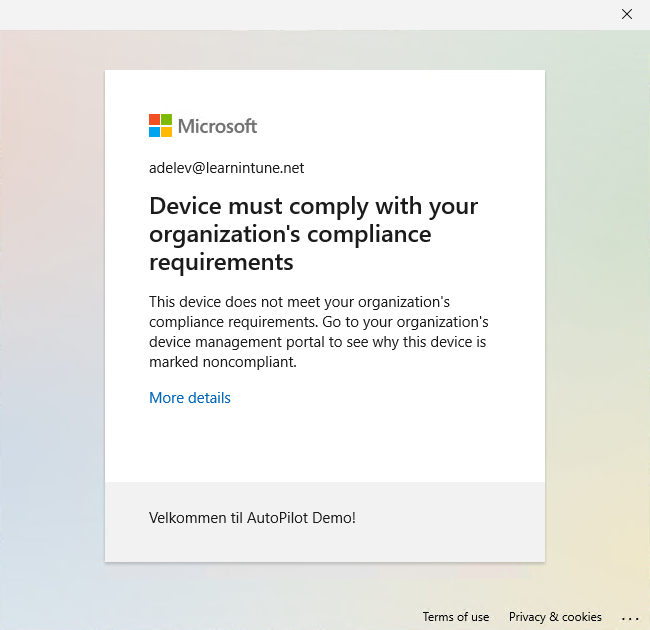
I have entered the credentials, and I'm now hitting the "Sign in" button. Luckily for me, it's now blocking Outlook with the below message.
I will now try with OneDrive to make sure it will apply to other apps than Outlook. I have entered my credentials and signed in.
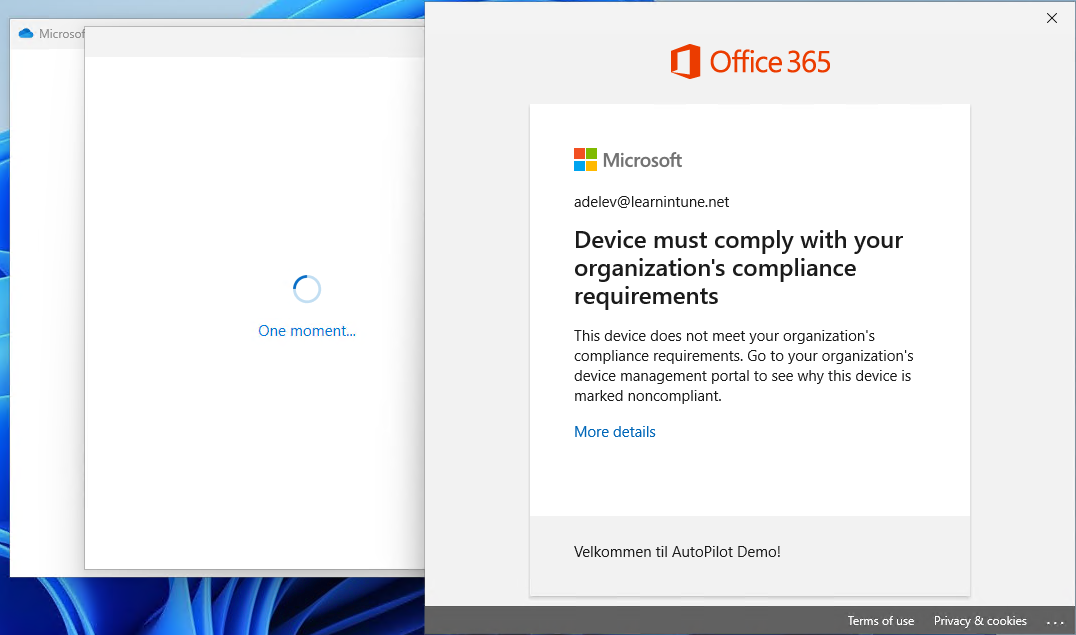
Wow, it works like a charm! That's great. Adele, from finance, cannot enter the desktop office apps on her personal device.
Observations pt. 2
I have made some observations that I thought would be helpful for many of you.
If you enter "edge://mam-internals/" in your Edge for Business browser, it will pop up with the below site.
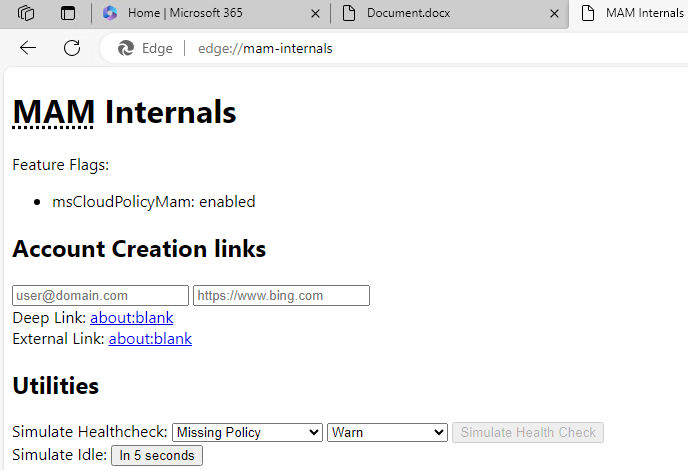
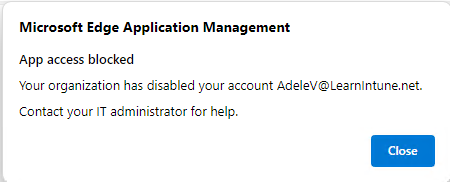
The interesting thing about this site is that you can simulate the health checks from your "App Protection" policy before applying them. Let's say you try to simulate an account that is disabled and the action is blocked.
Once you have modified it and clicked "Simulate Health Check", it will give you this pop-up.
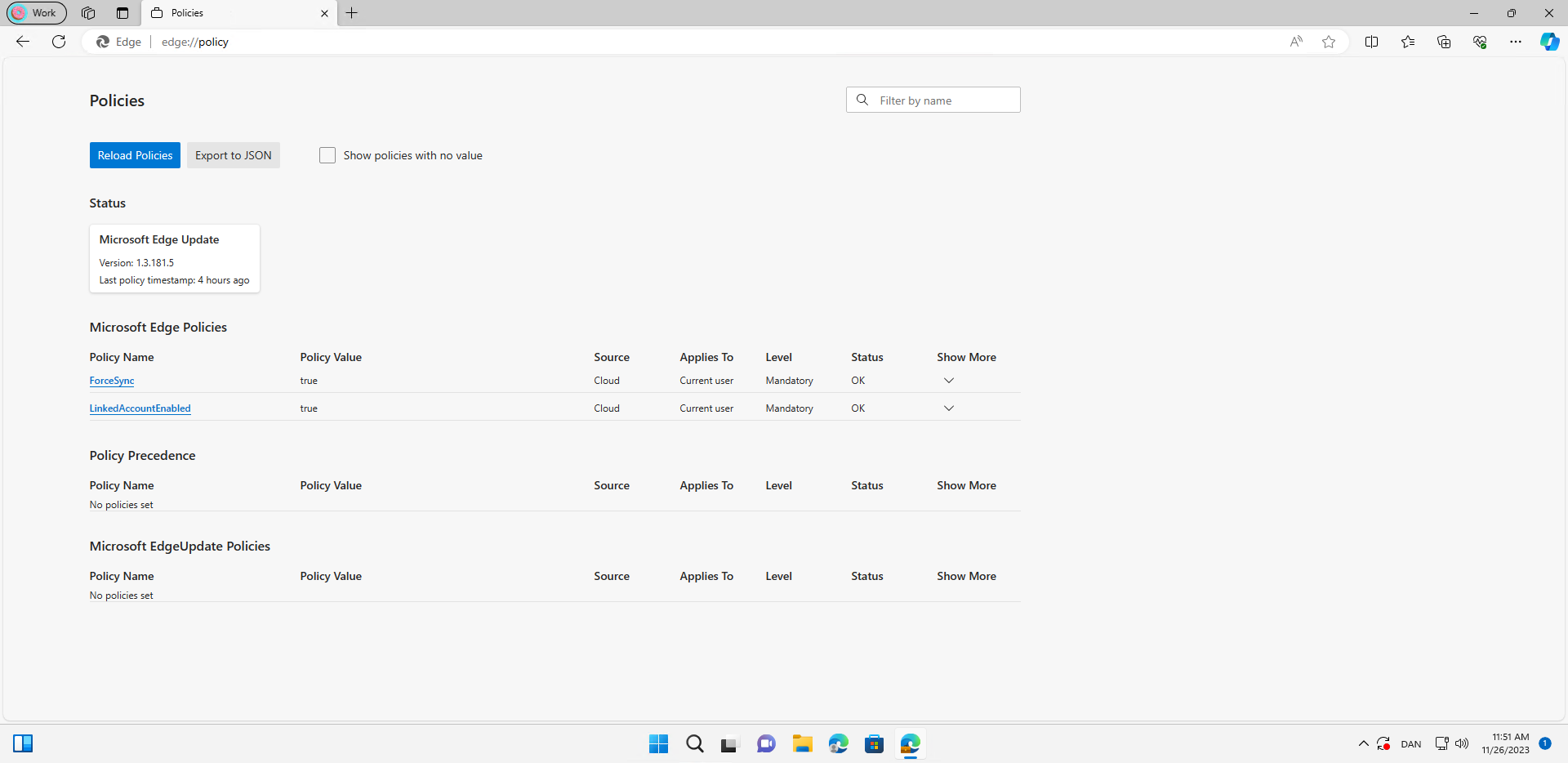
A cool feature that I have discovered as well is that you can see if your "App Configuration" policies have been applied.
I have now made a few policies targeting Adele, and I would like to see if they are applied. I enter "edge://policy" in my Edge for Business browser and can now see that my policies have been applied.
Conclusion
Thank you for reading this blog. This blog has been a tough one. I had issues with the CA policy being applied whenever a user opened a new tab, forced sync, or logged into Edge. However, MS seems to have fixed it before I finished the blog.
I hope you found this mini-series of MAM interesting.
